DCOM FUD: KB5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414)
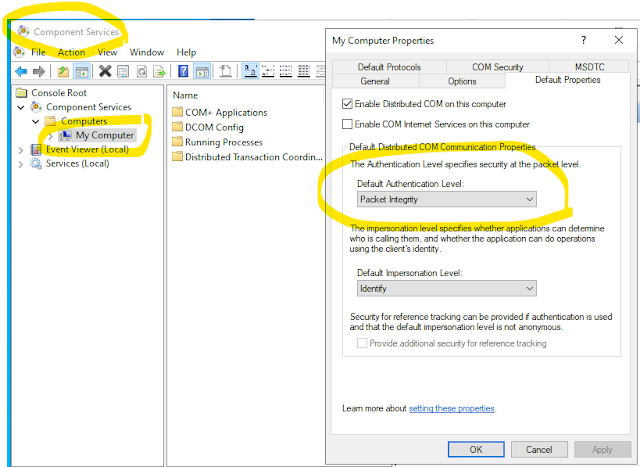
DCOM FUD Caused by KB5004442 Applies to Windows domain controllers that are setup as "Certification Authority" that are being used from domain connected workstations to perform user self enrollment to generate certificates for PIV smart cards. PIV smart cards are used to authenticate and logon. While setting up a DCOM application such as certificate enrollment services between workstations and servers, all running modern operating systems such as Windows Server 2022 and Windows 10, you start to see DCOM failures. And you see error 10036 in the system log. 10036 "The server-side authentication level policy does not allow the user %1\%2 SID (%3) from address %4 to activate DCOM server. Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application." (%1 – domain, %2 – user name, %3 – User SID, %4 – Client IP Address) This is a real error message from the test environment. The server-side authentication level policy
